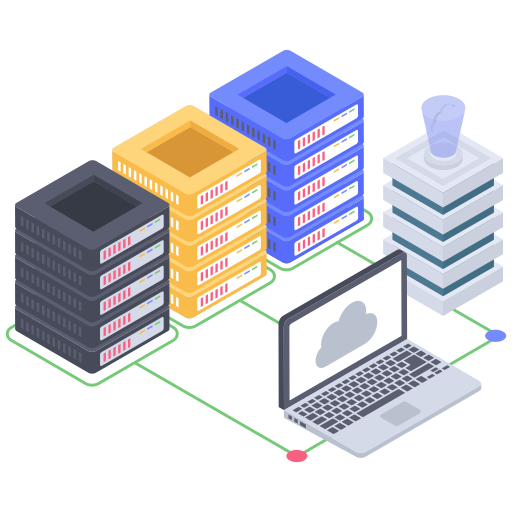
Easy way to manage
IT Services
in tech field within perfect time
online platform designed to help organizations manage their
operations, resources, and workflows more efficiently.

Let’s talk us
we’re available to make a cool conversation about your service that you want
Infrastructure Service

Cloud infrastructure refers to the hardware and software components — such as servers, storage, a network and virtualization software — that are needed to support the computing requirements of a cloud computing model. Datacenter and Private Cloud When it comes to storing and accessing massive amounts of data by your company or organization, cloud data services are a cost-effective alternative to
IT Products

Is a comprehensive software system that automates the hotel services call centers were all customer calls are received and redirected to the appropriate department for fulfillment and immediate follow up. Extensive reports are made for follow up and monitoring the quality of services offered. this system has many interfaces to other hotel vital systems.

integrated system
experts is dedicated to ensuring that your integrated system is up and running smoothly. We provide 24/7 support and maintenance services to help you troubleshoot issues and keep your systems running at peak performance.

Network
backbone of carrier-grade hardware and software, ensuring the highest level of reliability and uptime. We have multiple layers of redundancy and failover mechanisms in place to ensure that your connection stays up and running, even in the event of a failure.

Storage solution
designed to meet all of your data storage needs. Our solution is designed with scalability, reliability, and security in mind. We offer a wide range of storage options to fit your specific requirements, whether you need to store a few gigabytes or petabytes of data.

Servers
Our server offers custom channels, automated bots, and real-time notifications to keep everyone engaged. It includes voice/video channels, event scheduling, and easy file sharing. Custom roles, user profiles, and activity tracking ensure smooth management. We strive to provide a positive, inclusive environment for all members.

cloud server

IT network
Processor

5G Networks
IT Security
Refers to the practice of protecting computer systems, networks, and sensitive information from unauthorized access, theft, damage, and other malicious activities. In today's digital age, where technology has become an integral part of our lives, cybersecurity has become a crucial aspect of ensuring privacy and security online.

Security policies and procedures
Configuration management
Our Configuration Management service streamlines and optimizes your IT infrastructure by automating the tracking, deployment, and maintenance of system configurations. Ensure consistency across servers, applications, and devices while minimizing errors and downtime. With robust version control and centralized management, our Configuration Management solution enhances efficiency, scalability, and security. Take control of your environment, reduce manual intervention, and maintain a reliable and standardized IT landscape with our Configuration Management service.
Security monitoring tools
Our Security Monitoring Tools offer comprehensive real-time threat detection and analysis, ensuring the continuous safeguarding of your digital assets. With advanced intrusion detection, anomaly detection, and log analysis capabilities, our tools provide proactive defense against cyber threats. Gain visibility into your network's security posture, respond swiftly to potential incidents, and fortify your defenses with our state-of-the-art Security Monitoring Tools. Stay one step ahead of cyber threats and protect your organization's sensitive information effectively.
Physical access control.
Our Physical Access Control system provides a robust and secure solution for managing entry and exit points within your premises. Utilizing advanced authentication methods such as biometrics, keycards, and PIN codes, our system ensures only authorized personnel gain access. With real-time monitoring and audit trails, you can track and manage physical access efficiently, enhancing overall security. Whether for offices, data centers, or critical infrastructure, our Physical Access Control solution offers a reliable and customizable means to safeguard your facilities and assets. Restrict unauthorized entry and bolster security with our cutting-edge Physical Access Control system.

Trusted by popular companies
Some of brands that we worked with in collaboration



Management solution

Systems management is the administration of the information technology systems in an enterprise data center. An effective systems management plan facilitates the delivery of IT as a service is the practice of initiating, planning, executing, controlling, and closing the work of a team to achieve specific goals and meet specific success .
Security Information and Event Management
Database Management
Cloud computing
Web App
50+ tools in tech industry